Enterprise
Password Vault
CyberArk (EVP)

CyberArk – Enterprise Password Vault (EPV)
A password vault is a software solution that protects any amount of passwords in a safe digital location.
The password vault encrypts the password storage and offers users the ability to pick a single master password that can be used to access the different passwords for various services and websites.
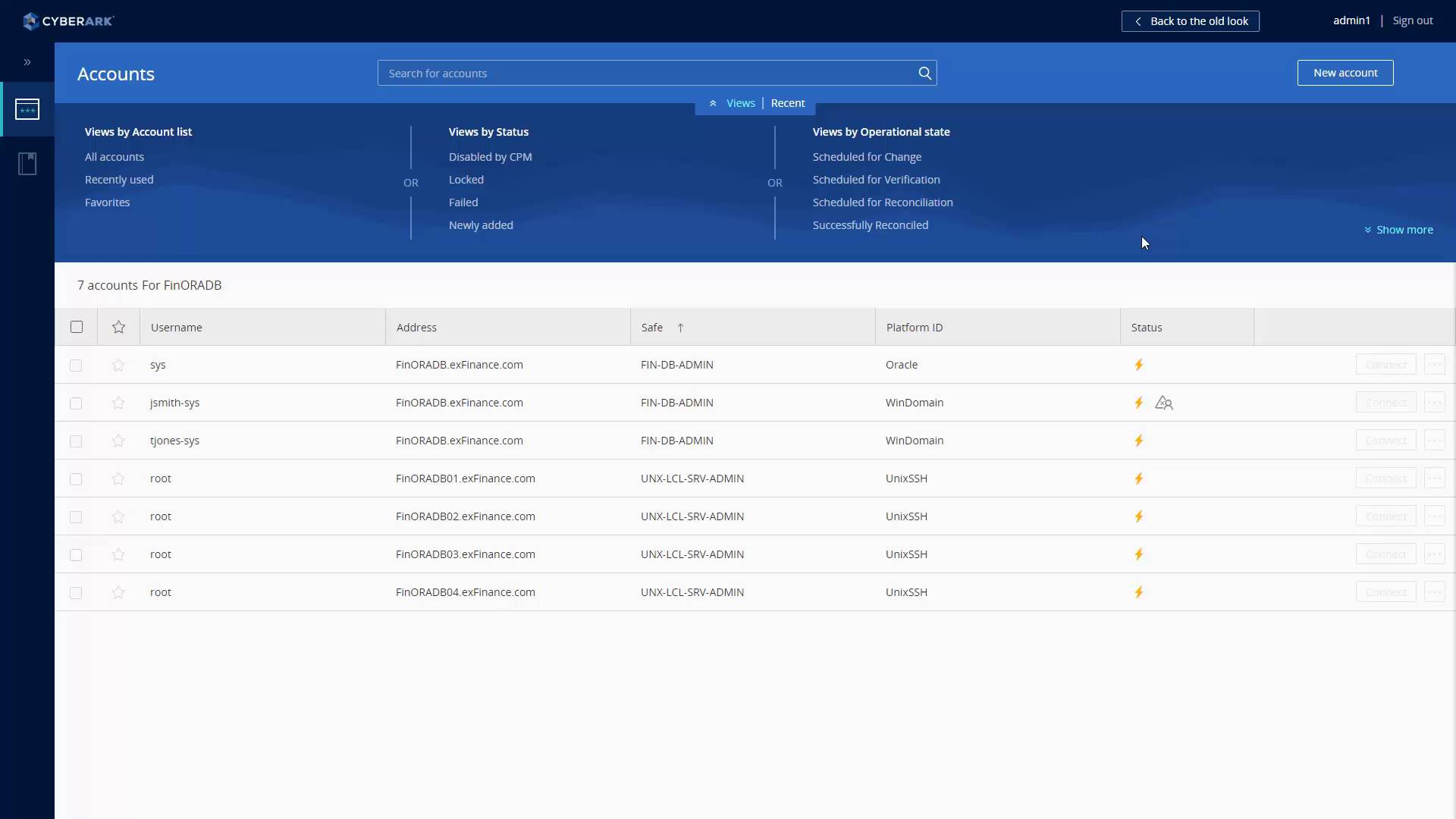
CyberArk’s Vault, also known as the Enterprise Password Vault is an application that enables users to manage their passwords in a central location for different systems used in a specific environment.
Access to an enterprise should only be given to a few privileged users in the form of passwords that oversee administrative access to applications and systems across an organization’s network. CyberArk’s EPV is one of the leading products that have been manufacturers with the sole purpose of managing and protecting passwords and controlling accounts across an extensive array of databases, client servers, switches, and mainframe OSes, among others.
CyberArk EPV provides individual account controls dictated by regulations, and its central network makes it the perfect addition to identity management projects. The vault also allows users to activate the correct paswo3f management policies that are essential to the management of the organization.
PowerBroker Identity Services Features
In fairness, the installation and configuration process can be considered tedious to untrained personnel. CyberArk EPV can improve with the addition of an installation manual and graphics-filled documentation to help users assess the functions of each component and their effects on the systems architecture. The current literature available to users is voluminous and complex.
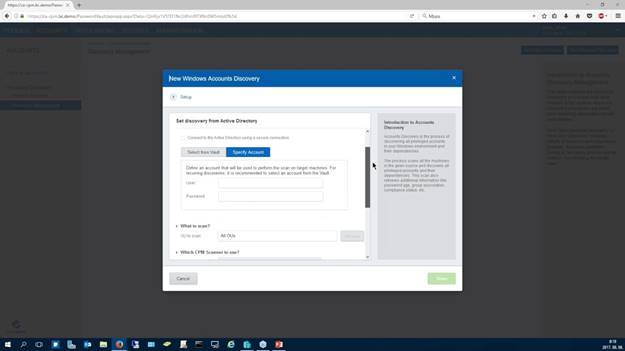
We expect that the quadruple components should be distributed across two Windows servers, with the inclusion of an overall diagram that references the different installations. For instance, the Password Vault Web is a sophisticated software solution that requires the experience of trained professionals, and our team has had the pleasure of installing components for clients who were frustrated with the installation process.
Quick tip: The IIS should always be installed on the second server. This information is not provided in the original documentation.
We are here for you
Allow us to help you pick the best of breed solution for your IAM Issues
Effectiveness Rating of CyberArk EPV
CyberArk EPV provides a wholesome experience once the installation process has been completed. Operationally, little to zero training is required for the end user password management system which is super intuitive and boasts of a wizard-driven interface.
The system is superbly spread out across the vault, which is fitted with multiple safes. Each safe operates independently and is often connected to a specific user or group. In some cases, both. A user in group A cannot see or access another safe without permission from Group B users. Each safe has single or multiple owners that control access. Passwords ate integrated with the bed products through each safe, such as switches, routers, and servers. Hence, changing the password for a particular safe will automatically adjust the end product access.
EPV assumes total control of the admin login function. When an admin accesses the EPV web interface to check the password object affiliated with a server they wish to change, the new object will automatically generate a new password that allows the user to access the switch and conduct their operation. Passwords can be created depending on the internal regulations and policies such as the Family Educational Rights and Privacy Act or FFIEC.
The system architecture is very reliable. This is an essential feature, but most enterprise security products don’t stand out with their security measures. Both the browser-based interface and vault shows zero vulnerability to cyber attacks or susceptibility to password leaks. Because of the firewall on the PrivateArk server, the host remains protected, and a single port is the only gateway for CyberArk’s proprietary protocol to be accessed.
Reporting Feature on CyberArk EPV
The reporting feature of CyberArk EPV is well executed; however there’s seems to be a drawback in the expert mechanism. Regardless, reports are presented concisely. The dashboard provides reports and graphs that showcase excellent auditing capabilities to fulfill regulatory requirements.
The single drawback in this aspect is the export mechanism. Reports can only be exported via CSV format and to Microsoft Excel and Word applications.
Pros
- Pinpoint and decrease the number of owner accounts
- Delete service accounts with non-expiring passwords
- Automatically replace privilege account passwords
- Automate reconciliation and password approval
- Regularly pinpoint, renew, and approve hardcover passwords
- Integrate Target Systems directly without showing users the passwords
CyberArk EPV Value For Purchase
- Eliminates the risk of external cyber attacks on privileged accounts
- Executive control over privileged accounts can be managed more effectively
- Privileged sessions can be recorded to identify the source of a breach or possible risks
- The automated system verifies and mages passwords to keep up with the constant creation and deletion of privileged accounts
Verdict
CyberArk’s EPV software solution is an impressive and valuable tool that does a great job of managing privileged password systems. It works well with fully patched servers on Windows 2003 and SO workstations. There are no signs of weakness regarding security, and it can withstand forensic analysis software and standard penetration testing tools.
“To be honest, I can’t find a service that I dislike from GCA.”
– Sr. Director Of Infrastructure, Education on Gartner Peer Insights
![]()
Start Planning For the Future Today
Book a 15-minute call with a GCA representative today to find out how an assessment can help you combat the challenges your organization is facing. We’ll discuss the interview process and set expectations for stakeholders.
Book a 15-minute IAM expert to get started.
