Data Privacy &
Security
Best IAM Practices

A New Business Standard
As remote work becomes the new business standard, identity becomes a key player in company security. However, establishing secure Identity & Access Management (IAM) practices requires not just technical changes, but shifts in business processes as well. Buy-in from leadership and awareness and training are critical to creating a zero-trust business culture with reliably secure identity systems.
Watch Jim Quasius (CEO, GCA Technology Services) walk you through the importance of data privacy and how you can set the foundation for a remote world.
Identity Is the New Perimeter
To empower users with the resources they need, organizations need to provide secure access to the data at its source. To accomplish this safely and efficiently, access needs to be carefully controlled, but not restrictive to the users that need it. This requires a highly strategic and expertly executed IAM plan.
Additionally, remote work is driving users to need data access from several disparate locations. Therefore, a functional IAM strategy often requires several solutions working together.
Enabling employees to access data in the cloud, for example, may require a different solution than granting access to data behind a firewall at the company data center. This requires a system of several solutions that work in tandem to protect data privacy via user identity.
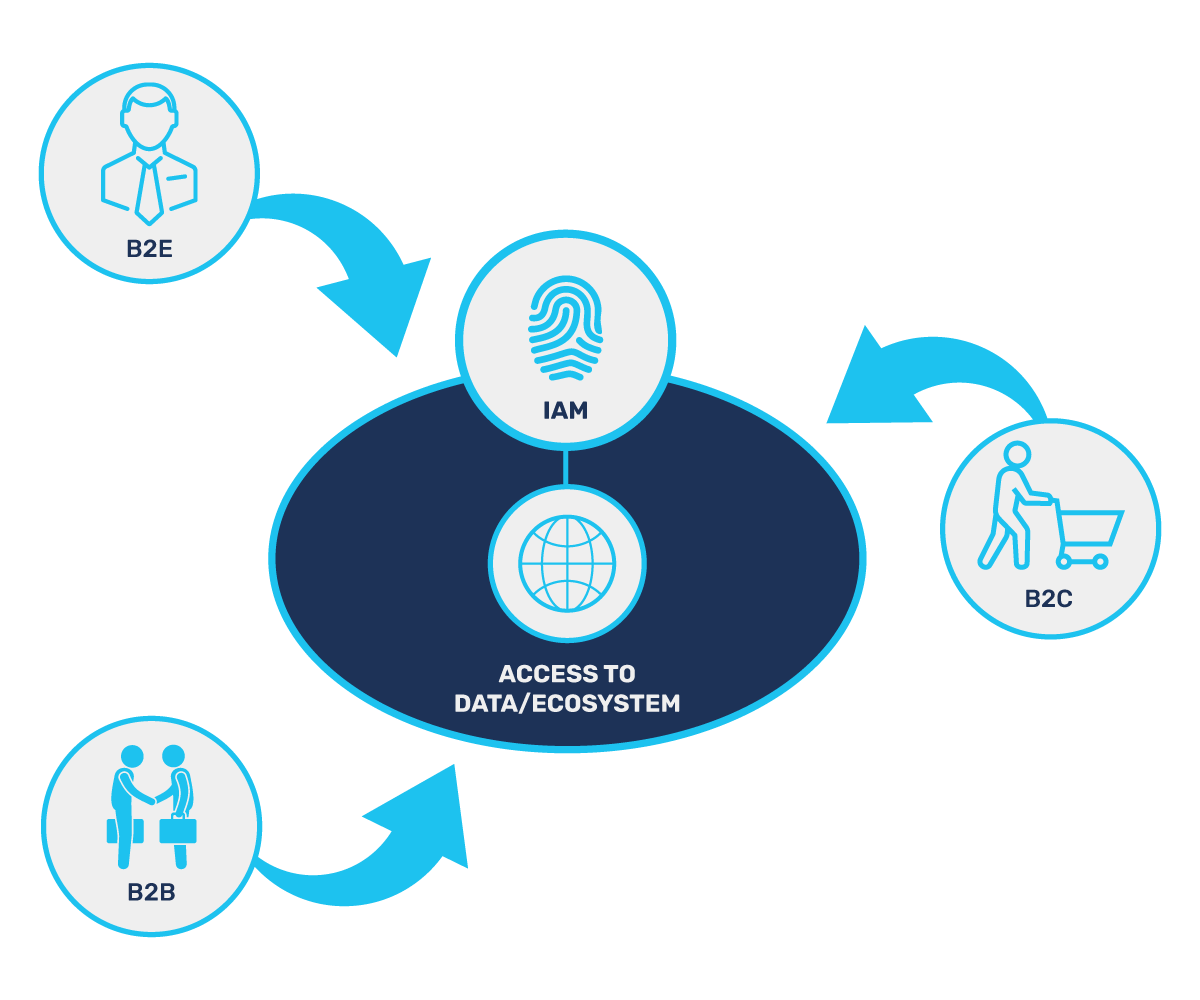
IAM Use Cases
Click Each Use Case to Learn How to Provide Seamless and Secure Login Experiences
B2E: Business to Employee
IAM at the employee level is foundational to organization-wide security, and usually one of the first IAM elements to be addressed. Employees need to be able to access the applications, systems and data they need while remote without compromising security. This requires air-tight employee identity management. A study by Gartner demonstrated that a company with 10,000 employees can attain ROI of nearly 300 percent and savings of $3.5 million over three years by implementing IAM tactics.
Example
Employees accessing applications and data.
B2C: Business to Consumer
B2C-level IAM includes customers, clients, patients and other individuals receiving services from the business. Consumers that access an organization’s data should be part of the organization’s IAM system—both to provide them access to the data they need, and also restrict access to confidential data. Studies show 32% of customers abandon a brand on their first bad experience, so fluid IAM systems are critical.
Example
Patients accessing their data from a portal.
B2B: Business to Business
Businesses need to ensure vendors, partners, stakeholders and other third-party entities are following IAM protocol to prevent a breach. Though B2B is often one of the last IAM frontiers businesses address, it is a critical security point with the potential for serious ramifications. It can also save you money—Gartner estimates a 375% ROI over three years for a business with 50,000 external users.
Example
Vendor accessing applications or data.
The Supporting Structures
Organizations need not only the IAM methodologies to enforce data privacy, but the IT structures to support those solutions as well. Zero-trust, for example, is a “never trust, always verify” methodology that many organizations are using to address the IAM needs and challenges posed by remote work. However, not all organizations have the structures they need in place to implement a reliable zero-trust strategy.
Attempting to create an IAM strategy on a porous foundation can be just as detrimental as neglecting data privacy altogether. IAM methodologies built without the supporting structures in place to ensure a successful implementation can create significant gaps in security, which can cause serious damage to the organization.


The Risks of Non-Compliance
The penalties of non-compliance can be severe — ranging from customer distrust to public lawsuits — and almost any compliance or security breach will cause reputational and financial damage. Even small security holes (like forgetting to remove a vendor from your directory after ending a partnership) are large enough to let bad actors into your network, giving them access to your data and assets.
Don’t wait until after a breach to find the vulnerability. Start constructing your reliable, IAM-based data privacy ecosystem now.
Schedule a Free Workshop
Learn more about how IAM technology works and how we use it to protect organizations in our overview.