Implementing an access review program with enterprise software is a common IAM initiative that addresses regulatory compliance controls.
An example of a HITRUST control for access reviews:
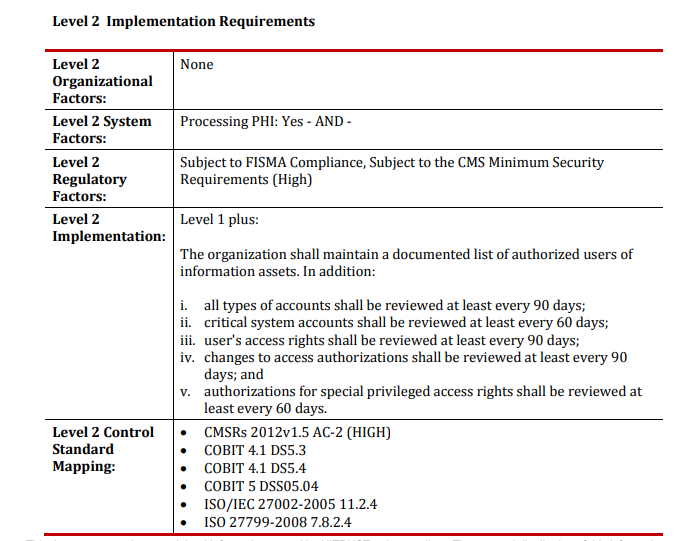
If your organization is due for an access review, read on to see what auditors look for so you’ll be sure to pass your next one.
Case Study: KPMG

GCA recently had the privilege of working with KPMG International during their audit process. Although processes may vary from one auditor to another, we believe this use case was a good example of a typical process.
First Meeting
The first meeting focused on a general understanding of how the access reviews worked and how the access tool worked. They wanted to know how we collected the information and how we knew the information was complete.
In this meeting, there were a lot of terminology and configuration discussions. It was almost as if we were giving a quick overview to a new technical resource who hadn’t worked with this particular product before.
Configuration
KPMG’s auditors asked us to provide evidence of the connectivity information to various applications in our access review program. We provided the auditors with screenshots from the connections configuration page.
With this screenshot, they independently validated that we were connected to the correct production system. If the screenshot was of an application where data was collected from a database, they would take note of the host server. They would then double-check that this server in fact hosted the production data that needed to be reviewed.
Identities
Next, the auditors scrutinized our connection to the authoritative source of users at the organization. They looked at our connection settings and confirmed they were from the correct production environment. They also spent time asking questions about the filter we used to pull in users. In this implementation, we did not want to pull in any disabled users as that would have majorly impacted license counts.
In addition to the configuration settings, we also sent a full export of identities collected with the filter we had configured. The understanding was that they took this list and independently verified our filter worked as expected.
Application Access
For some of the applications, the auditors requested the full review details from the previous year. Fortunately, with the access review tools, generating this report was simple. These access review tools were developed with the specific intent to ultimately please auditors.
Remediation
Finally, the auditors sent inquires about specific users and their access removal steps. Here they asked us to send evidence of the access review tool opening tickets to remove access in their ITSM tool. Like the other pieces of evidence, we collected the necessary screenshots and the auditors did an independent evaluation.
Pass Your Next Audit with GCA
These access review audits are taken seriously. They can be time-consuming, but the access review tools make the information readily available.
With GCA’s Compliance as a Service offering, we manage the entire access review program, which includes collecting evidence for the auditors. This saves organizations a lot of time and headache, as the auditors often want a lot of information. Learn more about our compliance services by contacting us today.



