Centralized
Database
Forgerock OpenAM

Forgerock OpenAM
Forgerock OpenAm approach to Identity access management is based on a systemic approach that combines all applications and systems under a centralized database.
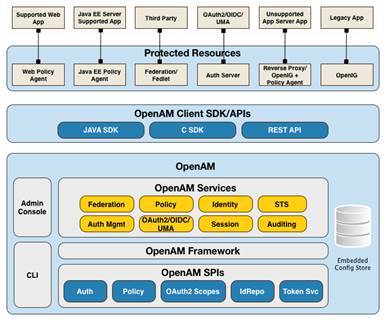
All you need to is download an deploy a single software that grants you total access management capabilities to manage access for all digital and physical entities.
As a business owner or executive at an organization, you get to control the system with a platform that allows you to create innovative products and services that are identity-based quickly. You don’t need to concern yourself with integrating new products on your platform thanks to Forgerock OpenAm security solution.
It acts as the bridge between web-based and mobile applications. You can utilize, deploy, and extend your control as needed without skipping essential deployment and procurement policies.
It is a given that irrelevant content irritates customers. The intelligent authentication feature of Forgerock OpenAM is designed to deliver dynamic content by driving personalization. Signals like locations, user device, and time can be utilized in real-time to create flexible web personalization content.
This notified downstream apps which helps you to develop offers that resonate with the expectations of your clients.
Stop Undermining Your Security with Unmanaged Access.
Talk to our SailPoint NERM experts today to design a strategy that brings comprehensive visibility and compliance to your extended enterprise.
Features of Forgerock OpenAm
Intelligent Authentication
Make each customer need the priority of your business strategy. By utilizing adaptive security intelligence, balance can be struck between customer choice and security to provide a well rounded, and meaningful experience across all digital touch-areas, at any time whenever you want.
Make the login process more accessible by offering flexible login choices and supporting FIDO. Smooth login options such as push notifications require additional steps in the login process only when compulsory.
Data-based insight allows you to upgrade and secure the consumer experience consistently. User login analytics combined with Intelligent Authentication provides timers and metrics that measure user interactions and their devices across applications and services.
Authorization
Employees and consumers want straightforward, comfortable, and secure access to resources, without the possibility of complex security protocols. Since the explosion of smart devices, IoT devices like pet doors and cars, switches, lights, and locks require advanced authentication and access management, now more than ever.
Forgerock OpenAm is designed to provide simple and extensible access and authorization protocols, from usual coarse-grained rules to powerful, fine-grained privileges with contextual understanding.
- Flexible fine-grained, and coarse-grained authorization – your pick
- Add and update policies quickly, without changing underlying applications
- Approve how IoT data is distributed based on privy information
- Attain access to physical resources, like buttons, doors, or switches with authorization
- Grant users delegated approval of their data between mobile, cloud, IoT, and other apps and locations via User-Managed Access function
Continuous Authorization
While most solutions only focus on initial authentication, Forgerock OpenAm allows contextual activity, adaptive risk, fine-grained authentication, push authorization, and multi-factor authentication during the authentication period as well as any time during a digital session
This continuous security approach guarantees the authenticity of services, people, and things at every turn and can limit risk whenever a breach is detected, even during current sessions.
Contextual Authorization
- Create context-based intelligence into protocols that safeguard resources during the duration of access, in addition to the authentication period
- Ensure verification of devices, users, services, and things always with a continuous and contextual authorization that can limit risk whenever an unusual pattern is noticed, especially during existing sessions
- Provide a platform to create secure and flexible policies that can assess risk whenever resources are accessed
- Create policy information points with scripts that are easy to write to attain a better understanding of the user and their context
- Use said context to monitor risks, thus, requiring advanced authentication mechanisms only when necessary. This makes it easier for users to access resources while maintaining system security
Adaptive Risk
The evolution of security threats is unprecedented in recent years. As people go about their daily lives with multiple devices, and complete various tasks on the go. To keep up with the stream of user data, it is essential to have an Identity Management solution that can respond to erratic behavior with quick, proactive measures. This is the basis of adaptive risk authentication.
Forgerock OpenAm regularly checks the authenticity of devices, users, services, and things in the system. GCA adaptive risk engine, combined with the software solutions contextual information to determine the possibility of a user attempting unauthorized access.
If access is deemed suspicious, am an advanced level of identity-proofing or authentication is requested. This can be appear as a one-time password.
You can rest assured knowing there are layers of advanced security to assess the authenticity of a user’s identity adequately. Even if a user logs in from an unrecognized device, OpenAm has you covered. Adaptive risks adapt to the evolution of security risks to help your organization stay ahead of threats without impeding user experience.
Adaptive Risk Allows You To:
- Monitor unusual patterns, and request for advanced authentication protocols when necessary to upgrade user experience while maintaining the integrity of the system
- Allow administrators to dynamically call and integrate third-party services, like LexisNexis, Guardian Analytics, FireEye Threat Analytics Platform, Equifax, and Esperian, for identity proofing
- Gain more knowledge of the user and the context of their login request. Every attempted login is evaluated in real-time and generates a risk score, based on factors including time zone, UP address, user location, account idle time, and time of day.
“To be honest, I can’t find a service that I dislike from GCA.”
– Sr. Director Of Infrastructure, Education on Gartner Peer Insights
![]()
Start Planning For the Future Today
Book a 15-minute call with a GCA representative today to find out how an assessment can help you combat the challenges your organization is facing. We’ll discuss the interview process and set expectations for stakeholders.
Book a 15-minute IAM expert to get started.
