SIEM LogRhythm
Worthy in the Leaders Quadrant

SIEM LogRhythm, Next Generation SIEM
LogRhythm is a threat detection product in security intelligence and analytics that allows organization around the world to identify, respond and effectively neutralize the effect of cyber attacks.
SIEM LogRhythm is a patented award-winning identity management solution that combines SIEM Management Logs with Advanced Security Analytics, and Network Forensics and End Ports. Furthermore, SIEM LogRhythm threat detection capabilities ensure automation for unrivaled Legal Compliance and Assurance, while boosting the understanding of your IT.
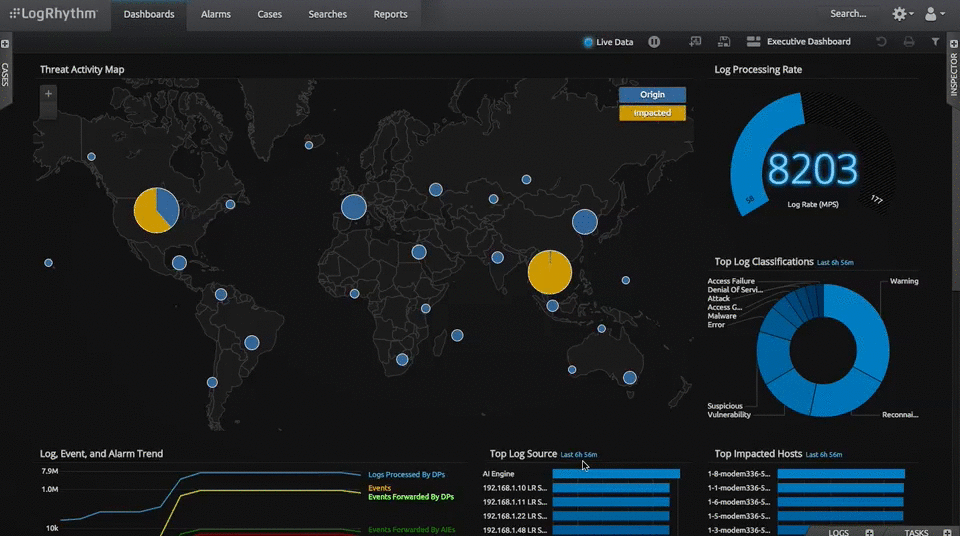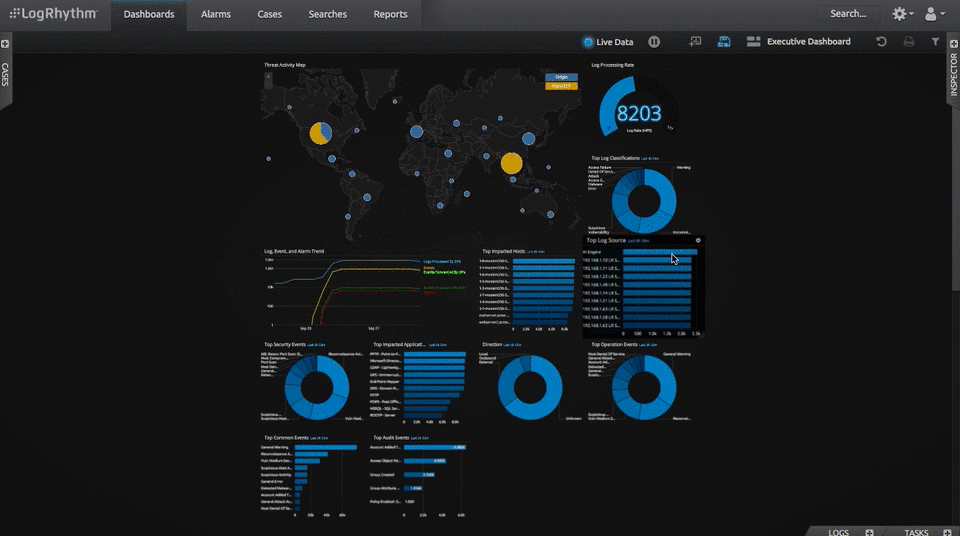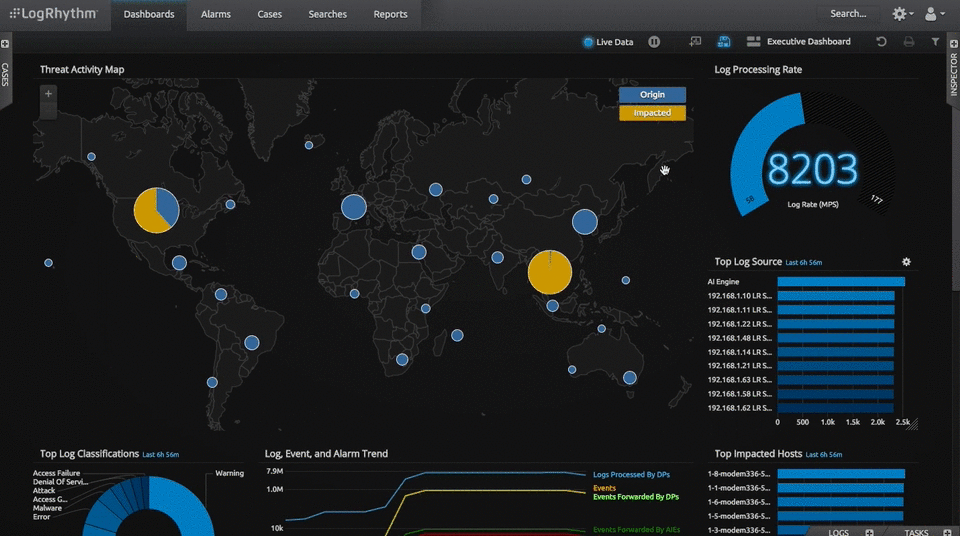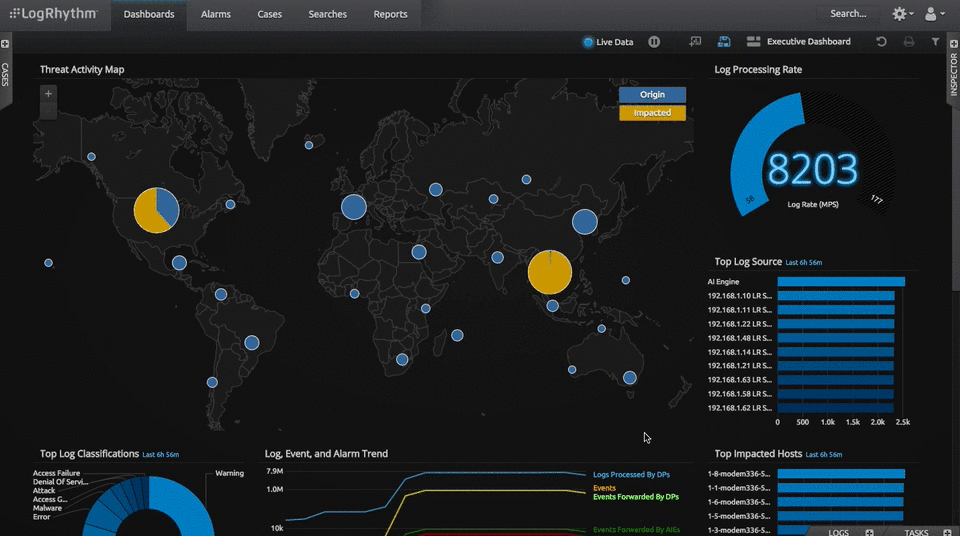
For seven years in a row, Gartner has found SIEM LogRhythm worthy to be in the Leaders quadrant. As data breaches continue to plague large enterprises, IT security teams need a SIEM solution that offers native options, host-and-network level monitoring, workflow automation, and industry-leading analytics. SIEM LogRhythm excels in all categories by quickly identifying and neutralizing security risks targeting an enterprise.
At GCA, we consider this software solution a leader in catering to the need of enterprises who want an in-depth analysis of corporate log files and wholesome security measures.
Scale With LogRhythm SIEM Comprehensive Solution
Regardless of the surrounding environment or size of your company, or whether your organization is in the middle of an expansion, or if short term goals must be met – including the inevitable extension of scope, SIEM LogRhythm is adaptable enough to be included to the list of additional devices without disturbing the usual rhythm of your organization. Also, LogRhythm SIEM threat detection remains the most comprehensive solution that allows customers to simplify, centralize, and strengthen their Security, Compliance, and IT operations on a single platform.
- Powerful Forensics
Discover and pinpoint suspicious activity in your networks. Analyze and protect your data, and exploit loopholes in your system before hackers take advantage of them - Ease of Use
Natural expansion and integration combined with a user-friendly interface that provides detailed security alerts and reports to simplify your action points, while strengthening the security of your network - Real-time Monitoring
You can track your operations simultaneously while LogRhythm SIEM manages, verifies and exploit threats in real-time - Fast Installation
LogRhythm can be installed and commissioned within 30 minutes without interrupting the regular flow of operations
We are here for you
Allow us to help you pick the best of breed solution for your IAM Issues
Program and Prevent Incidents
LogRhythm SIEM provides you with the option to choose automation times for security incident management and research methodologies. The SmartResponse feature is useful when scheduling answers and to prevent breach incidents.
Results and Analysis Effective
LogRhythm SIEM uses unstructured and contextual analysis to identify threats and analyze events in your systems. LogRhythm analytics provides you with accurate data to identify and exploit gaps in your networks.
Provides Protection and Tranquility
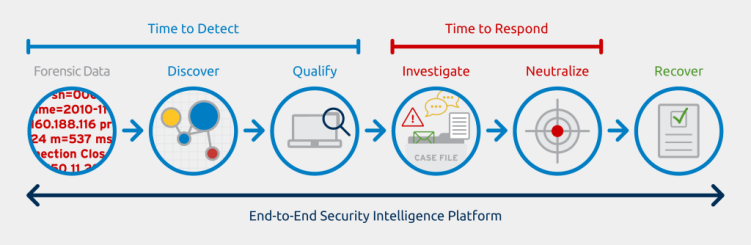
LogRhythm laboratories developed specific modules that offer comprehensive and trailblazing protection to your assets and networks. Its capabilities allow it to promote safety and peace of mind. Let’s create a scenario where your team is struggling with the influx of logged incidents. You need your security operation to be more efficient. LogRhythm SIEM is the only SIEM solution tailored to provide response workflow and end-to-end threat detection, which is referred to as Threat Lifecycle Management. The platform offers a lower cost of ownership and streamlined operations.
LogRhythm Focuses on the Threats, Not the Tools”
- Automated Machine Analytics: Software focuses solely on the collation of forensic data and security events. Your security team will receive real-time, detailed intelligence into risk-prioritized attacks
- Network and Endpoint Monitoring: Get in-depth insight into network activity and endpoint with integrated forensic sensors. You can identify behavioral anomalies and react to incidents faster and more efficiently
- Case and Security Incident Management: Ensure that high-level threats don’t find loopholes with collaboration tools and integrated workflow that centrally track and manage incidents and investigations
- High-Performance Log Management: Efficiently index and process terabytes of log data daily. Immediate access to machine data and contextualized in support of investigations. Both structures and unstructured findings provide concise and sophisticated analysis to your system
- SmartResponse™ Automation Framework: Execute pre-determined actions centrally to cause the incident response remediation and the automation of investigatory tasks
“To be honest, I can’t find a service that I dislike from GCA.”
– Sr. Director Of Infrastructure, Education on Gartner Peer Insights
![]()
Start Planning For the Future Today
Book a 15-minute call with a GCA representative today to find out how an assessment can help you combat the challenges your organization is facing. We’ll discuss the interview process and set expectations for stakeholders.
Book a 15-minute IAM expert to get started.
