Dominate Your
Datacenter
CyberArk (PSM)

CyberArk – PSM
Privileged accounts like Sys on Oracle, Administrator in Hypervisor and Windows, UNIX, and others are dominant in all your datacenter.
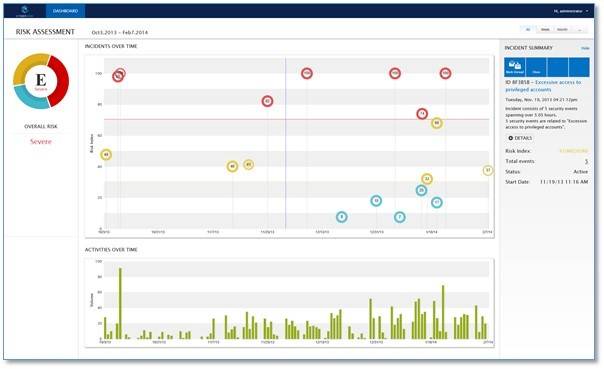
This patented analytic technology is applied to a unique set of privileged account behavioral data, and CyberArk PTA produces streamline and highly actionable intelligence that alerts the incident response teams to the point of attack. The data is also sent to existing SIEM solutions to upgrade the effectiveness of response and quality of alerts.
Why Choose CyberArk PTA
CyberArk has the honor of being the only company that can provide total protection against insider and advanced threats to eliminate risks and fulfill high-end compliance requirements. The product can boast of more deployments in large scale virtual and distributed environments, having solved many privileged account security issues than any other software solution.
These accounts give you a chance to manipulate and allow access to all your sensitive business information with fantastic business returns. Privileged accounts are so good that they’ve been the target of both external and internal attacks.
How many times have you been concerned about the users of these privileged accounts and if they’re using it the right way? Or maybe you want more control on the people that connect to these accounts, especially the third party vendors or you might want to know the cause for the disruption in your production system by checking all the administrative activity carried out before the interruption.
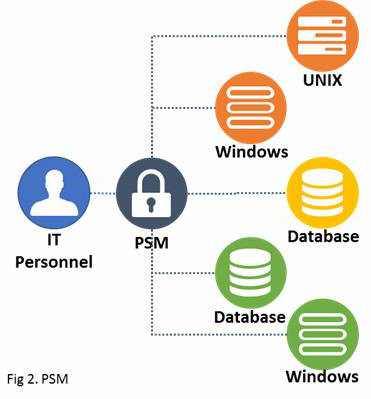
CyberArk Privileged Session Management (PSM) is a popular central control point that helps to protect target systems that are accessed by privileged accounts users throughout your data center. It usually works in conjunction with the CyberArk market-leading Privileged Identity Management Suite, an enterprise and a policy based solution that enforces, manages and secures workflows and procedures for all shared and privileged accounts in data centers.
Stop Undermining Your Security with Unmanaged Access.
Talk to our SailPoint NERM experts today to design a strategy that brings comprehensive visibility and compliance to your extended enterprise.
How Does CyberArk Privilege Session Manager Work?
The architecture of Cyber-Ark’s PSM is proxy based and the server proxies the connection to the target. The privileged session Management doesn’t require any agents on the target systems, and won’t have any footprint on the IT infrastructure of the organization.
The end-user will describe accessing a target system as just logging on to a password Vault Web Access (PVWA) portal, and just finding the target system to be used to connect and tapping on the “connect” button. The session could also be opened from a desktop. The following steps should be performed to start a session under the hood:
- User use the Web portal (PVWA) to log in and also a choice of utilizing the 2-factor authentication
- The user looks for the target system. The Vault access control gives the users a chance to access and see only the system he’s entitled to. The solution provides the machine with on-demand temporary access, e.g., for 3rd party vendors, without releasing the privileged credentials. Also, the solution can induce approval validation or workflow against ticketing and transforms control systems to approve the request.
- To connect the target system, the user presses the connect button on the PVWA. The server of the PSM proxies the connection to target systems and insert privileged credentials needed to initiate a session to the required device. It is crucial to note that the credentials don’t reach the end user’s browser, therefore, remains secure.
- After this, a session is opened to the target system without needing a specific connection password. The user will be able to work on the target system without problems.
- The activities of the session will be recorded by the PSM Server, and when the session ends, it’ll be securely suite in a tamper-proof, secure floor preserved in a highly compressed format (about 70kb/min for console sessions and 200kb/min for GUI sessions).
- Sessions events (SSH keystrokes, SQL commands) are well-written to a Vault audit and will also be sent in real-time time to a SIEM solution for automated responses and further analysis.
Why Your Business Needs PSM
You can use the PSM to:
- Build a strong authentication to a PSM portal before it accesses critical servers
- Provide access workflows like dual control approval
- Integrate with ticketing systems and change controls
- Control access to servers with policy-based access control
- Make restrictions on the privileged session duration
- Notices privileged sessions with the ability to terminate with suspicious sessions and interact with them
- Control access to servers using policy-based access control
- Leverage P-SSO capabilities for IT Contractors to enable temporary and ad-hoc access for non-internal personnel that might not have the same level of trust with your internal personnel
- Connect to the various target system through the Privileged Single Sign-On (P-SSO) – the connections to target systems will be performed without exposing the connection password
“To be honest, I can’t find a service that I dislike from GCA.”
– Sr. Director Of Infrastructure, Education on Gartner Peer Insights
![]()
Start Planning For the Future Today
Book a 15-minute call with a GCA representative today to find out how an assessment can help you combat the challenges your organization is facing. We’ll discuss the interview process and set expectations for stakeholders.
Book a 15-minute IAM expert to get started.
