OpenText/NetIQ
Identity Manager (IDM)
Identity Manager

OpenText/NetIQ – Identity Manager (IDM)
It can be frustrating for users on a system when they are unable to access information on work computers or their mobile device. This usually occurs when you forget your password or when you forget the answer to a security question.
Data security is vital regarding information about your company and your customer’s private information safe. Depending on the type of data stored, there are government mandates that require data security.
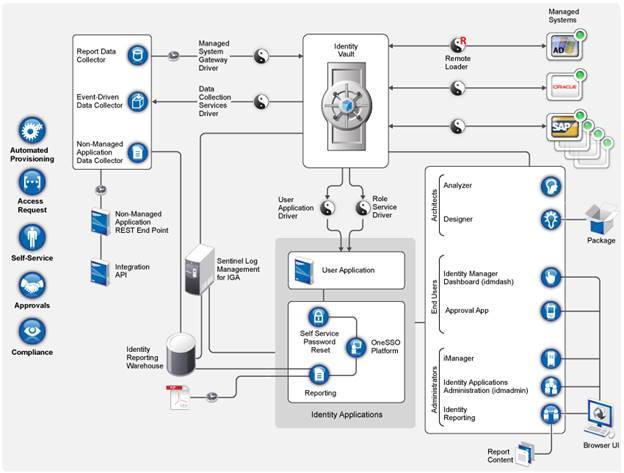
Wouldn’t it be great if you had a tool that allowed immediate full access to the information you needed while at the same time securing your data in compliance with government mandates? This is precisely what OpenText / NetIQ – Identity Manager has been created to help you accomplish.
OpenText / NetIQ – Identity Manager, formerly MicroFocus Identity Manager, is a cost-efficient, easy to integrate, and flexible solution to many of your data security concerns. It makes it possible for you to control who has access to protected information and adjust that access as the roles of your employees change while at the same time making it easier for you and your authorized employees to quickly and securely access your data.
The following are a few of the positive features that OpenText/NetIQ – Identity Manager offers that makes it outstanding.
We are here for you
Allow us to help you pick the best of breed solution for your IAM Issues
Features of OpenText/NetIQ – Identity Manager (IDM)
1. Comprehensive Support for Security and Compliance
Identity Manager makes it easy for you to secure information whether you have it stored on-premise, on the cloud, or in a hybrid environment. The reports it generates allow you to prove that your data is secure in harmony with in-house, industry, or governmental mandates.
Identity Manager monitors security compliance in your enterprise, even if you have thousands of users. This technology offers resources that extend from the data center to the cloud. It works seamlessly with your security event and information management systems as well as any applications you and your employees are using. The result is continued compliance throughout your entire enterprise at a relatively low cost.
Here’s an example of how this technology works. Steve has been with your business for many years and has been granted access to sensitive information and applications. As a result of misconduct, Steve is terminated, but he is not happy about it. Could Steve use the access that he has to your enterprise’s sensitive data for an attack?
Not if you are using Identity Manager. As soon as Steve is terminated and a change in his status is entered into your HR system, Identity Manager immediately removes his access to your company’s, information, applications, etc. This change is propagated throughout every resource your enterprise uses, including physical assets, databases, directories, cloud-based applications, and email systems.
Identity Manager gives you complete control over what privileges your employees have. Let’s say Sally is assigned a temporary project that requires her to have access to sensitive information in the accounting department. Identity Manager maps out the privileges that Sally has. This allows your business managers to see all of her rights on one screen, make changes to her privileges, and then once Sally’s temporary assignment is over, those temporary privileges can be removed. This means that you don’t have to worry about multiple identities for one user.
2. Simple to Deploy
Identity Manager is easy to install. Integrating into your current data security structure is simple. Configuring Identity Manager components is straightforward. This means that as soon as your enterprise is ready to take advantage of this tool, you can begin implementing it.
3. Automated Provisioning for Easier Administration
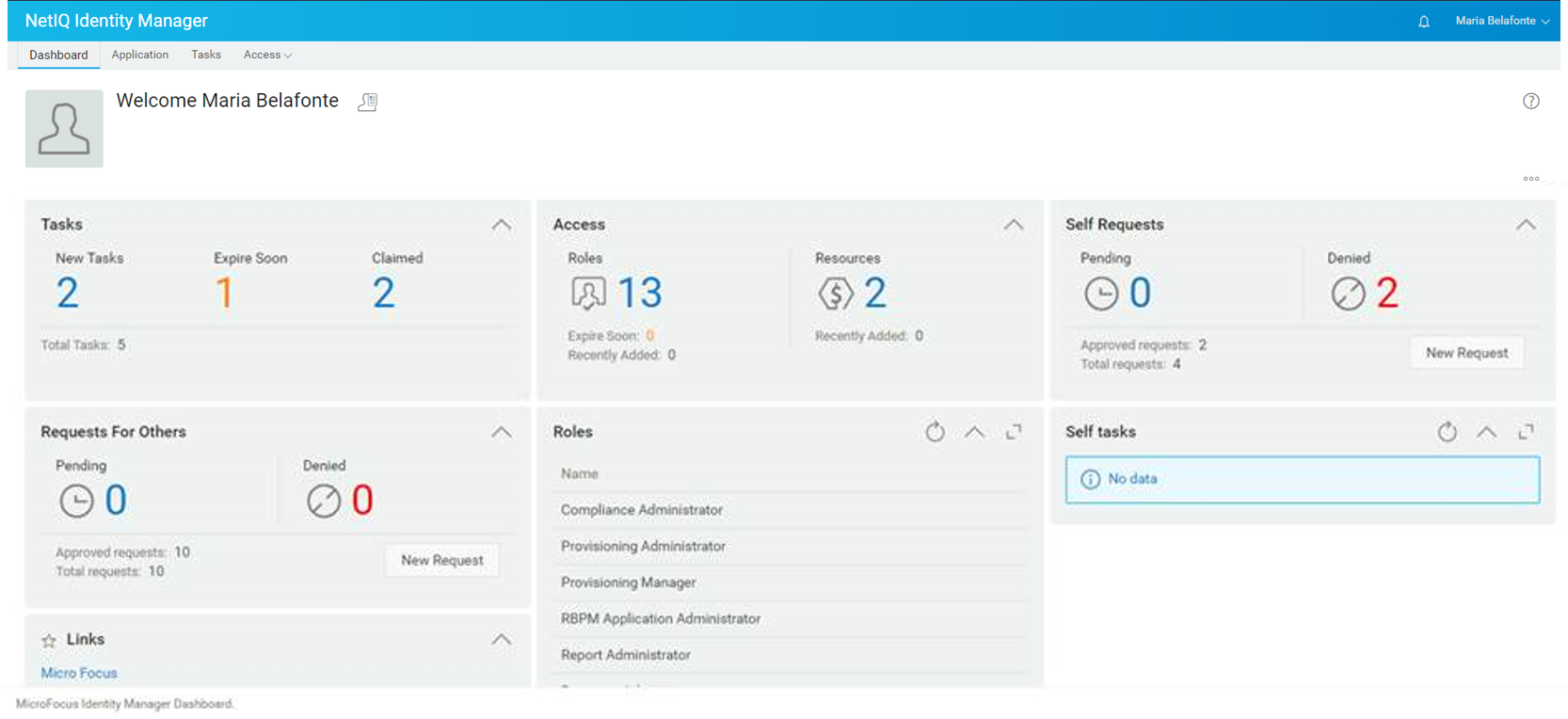
Identity Manager minimizes the costs, risks, and frustration that come from having people trying to manage the identities of users throughout their lifecycle manually. In enterprises that have thousands of employees, doing this work manually and efficiently is all but impossible.
The automated provisioning and de-provisioning will save your business managers countless hours. When your employees transfer between departments, move on to work for another company, or when a new user joins your enterprise, quick provisioning actions, based on the policies you have put in place, are automatically triggered. Your users’ access and privileges are changed instantly and accurately.
Once the automatic change is triggered, it is stored in the Identity Vault. This is the authoritative data store. From there, the change is propagated through all of the physical and virtual resources your enterprise has. A change in a user’s access will even affect the applications you have stored in the cloud.
Identity Manager will provide you with detailed reports that show you who had access to what information or what application at any given time. So, if a few years down the line an auditor has a question about the access Sally had to the accounting department during her temporary assignment, you can easily pull that information up and create a report that proves that your business complies with internal policies as well as external governmental regulations.
4. Single Sign-On Support
Earlier, we discussed how frustrating it is to be denied access to information you are authorized to use because you could not remember all of the passwords or security questions you have. Single sign-on support makes that problem a thing of the past. Now, you and authorized employees will be able to log in to various applications your enterprise uses with just one login.
OpenText/NetIQ – Identity Manager is a technology that is designed to be intelligent, efficient, and future looking. Currently, it is the only cloud-ready identity management service. This means that you can extend your identity management to resources that are beyond your enterprise’s firewall.
For more than ten years, OpenText has offered many technologies across operating systems and platforms designed to make it easy to secure your enterprise’s private information. By leveraging the security policies that your enterprise already has in place, Identity Management allows for sustainable SaaS solutions.
“To be honest, I can’t find a service that I dislike from GCA.”
– Sr. Director Of Infrastructure, Education on Gartner Peer Insights
![]()
Start Planning For the Future Today
Book a 15-minute call with a GCA representative today to find out how an assessment can help you combat the challenges your organization is facing. We’ll discuss the interview process and set expectations for stakeholders.
Book a 15-minute IAM expert to get started.
