Advanced Authentication
Framework (NAAF)
OpenText / NetIQ

OpenText / NetIQ
These data breaches expose the private information of clients, reveal the financial information of the company, and tarnish the company’s reputation.
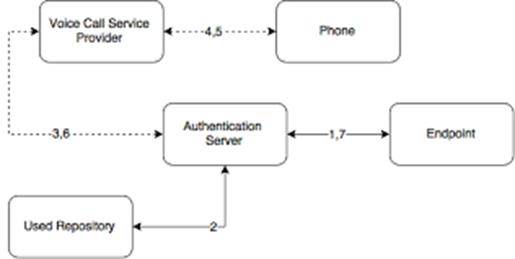
OpenText / NetIQ – Advanced Authentication Framework (NAAF) provides a framework that allows you to move beyond usernames and passwords and take advantage of a more secure and advanced multi-factor authentication throughout your enterprise.
We are here for you
Allow us to help you pick the best of breed solution for your IAM Issues
OpenText / NetIQ – (NAAF): Essential To Organizations?
You can answer that question by just walking around and visiting the offices and cubicles of your employees. Do they have log books full of passwords? Are whiteboards, that are seen by anyone who walks by, used to store usernames and passwords? Are desks and computer monitors covered with sticky notes that your employees use to help them remember usernames and passwords?
If the answer to these questions is yes, you are just a step away from a data breach. OpenText / NetIQ – Advanced Authentication Framework (NAAF) can help you.
Multi-factor authentication is a safer way to allow your employees to access the information and applications they need to get their jobs done.
Questions that need to be answered:
- Does this mean that you have to make sure that all of your employees have expensive card readers or biometric scanners at the ready?
- How do you implement multi-factor authentication for mobile workers or those outside of your company who don’t have access to the right readers, such as contractors or vendors?
- What about people who do not have smartphones?
- How do you make many multi-factor authentication technologies work together?
These are challenging questions. However, the answer to them all is OpenText / NetIQ – Advanced Authentication Framework. This framework is designed to support all of the latest methods and technologies.
This platform allows you to create a single set of unified security policies that can be used to manage employees, vendors, customers, and other unique scenarios.
Ideal Scenarios for OpenText NAAF Deployment
- Within the office setting, employees who have a badge can scan their badge and then enter a pin to gain access to the data or applications they are entitled to.
- Mobile employees, contractors, and vendors who have biometric readers on their laptops can use those to authenticate their access.
- If a user loses or forgets their ID badge, they can still login by requesting a challenge and response.
- A user can use their smartphone as a multi-factor authentication tool by receiving a one-time SMS password that they can use to log in.
Your company’s personnel now have the flexibility to use the best multi-factor authentication method that works at that particular time and in the environment that they are in. So, an employee who is temporarily working in the field may opt to use the biometric reader on their laptop. When they return to the office, they may scan their badge and enter a pin to get access to what they need to work on.
Benefits of OpenText / NetIQ – Advanced Authentication Framework
Firstly, new technologies become available, and they can be integrated into the framework and start to be used right away. This means you and your staff can say goodbye to weak usernames and passwords for good.
- Docker-based Containers for Maximum Flexibility: This means that regardless of the operating system you are using, Advanced Authentication can be employed. Docker containers are seen as the preferred way for distribution in cloud environments.
- One Framework for All Your Authentication: Your organization likely manages many authentication infrastructures. They are challenging to manage and present unique security risks. This technology offers you a single authentication framework for all of your devices and all of your methods.
- Authenticate to the Appropriate Level of User Verification: Within your organization, there is specific information that is more sensitive than other data. The sensitivity of the data will determine the level of authentication you are going to want your employees or managers to provide before gaining access to it. For example, for financial information, you may require that your employees be on premises, use a known device, and meet other criteria before they are granted access.
- Second Factor Skipping: You want a balance between security and speed of access. This feature allows you to do that. You can require your employees to fulfill the complete authentication requirement initially. Then they can be granted a grace period where they can re-access the information or application without needing the second-factor authentication. This can be adjusted based on the sensitivity of the data being accessed.
“To be honest, I can’t find a service that I dislike from GCA.”
– Sr. Director Of Infrastructure, Education on Gartner Peer Insights
![]()
Start Planning For the Future Today
Book a 15-minute call with a GCA representative today to find out how an assessment can help you combat the challenges your organization is facing. We’ll discuss the interview process and set expectations for stakeholders.
Book a 15-minute IAM expert to get started.
