“Reverse Proxy” has an intimidating name, but that is where the complication ends. It is an easy concept to understand. In this article we will define, discuss, and unwrap a reverse proxy.
Let’s Use an Analogy
Restaurants provide a nice analogy for explaining reverse proxy technology. Lets compare some big national brands that everyone should know, McDonalds and Applebee’s. The use case both of these companies meet is feeding people who are hungry. In this analogy the process of eating would be equivalent to logging into SalesForce.

At McDonald’s anyone can walk in the door and take a seat at a table. There is no structure to it. This is how access to SalesForce would happen without a reverse proxy. Users could be at the office, on the couch at home, or on vacation in Tahiti. In each situation the function is the same, users type in SalesForce.com and they go directly to their account, just letting walking in McDonalds and grabbing a seat.
The difference between McDonald’s and Applebees for this analogy is the introduction of a Host or Hostess. Now instead of going directly to a table there is a person in the middle who controls the traffic. There is a person who runs algorithms and then takes hungry people to their destination. The benefit here is that the tables have a bit more protection. If someone walks in with no shoes and no shirt the host or hostess will be able to block that person’s access to the dining room tables. At McDonald’s with no hostess available, our shoeless and shirtless friend can waltz in and take any seat that is available.
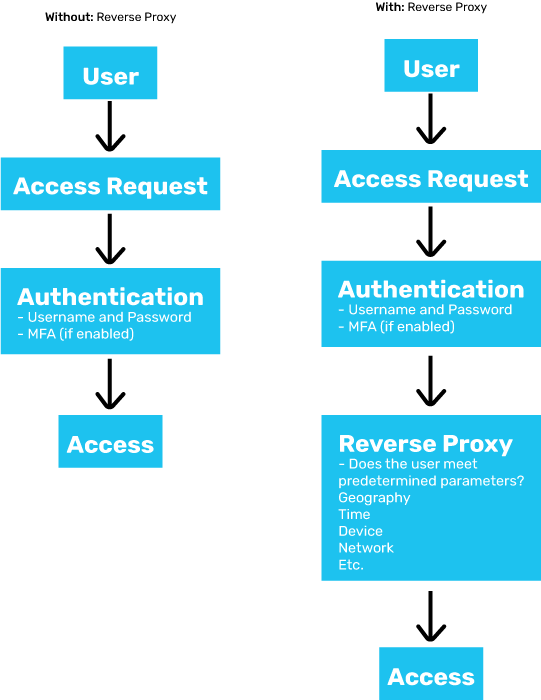
Reverse Proxy is a Gatekeeper
This is what a reverse proxy’s primary function is, to be the gate keeper. Instead of checking for dress requirements the reverse proxy technology can make decisions like:
- Is access to SalesForce acceptable at 3am on a Saturday?
- Is access to SalesForce acceptable for a US based employee to come in from Saudi Arabia?
- Should we ask for additional information (MFA) before letting this person login to prove who they are?
In Access Management what happens is a sophisticated host or hostess is put in place between users and resources. By funneling all traffic through a reverse proxy organizations can apply the business logic needed to secure their environments.
Reverse Proxy and Zero Trust
From a zero trust perspective a reverse proxy can greatly reduce the attack surface. Sticking with SalesForce.com if your organization is not using a reverse proxy there are 7 billion people who could attempt to access your accounts. However SalesForce, even thought it lives in the cloud, can force all authentications to your organizations instance to funnel through your reverse proxy / access management solution. With this configuration a user would need to authenticate before the reverse proxy even starts talking to SalesForce.com. Now your attack surface has been reduced from 7 billion people to the number of active credentials at your organization.
Start Protecting Your Applications
Reverse Proxy serve as a fundamental building block for securing organizations. At GCA we have a team of experts who can assist in setting up your organizations access management program.



