Privileged Threat
Analytics
CyberArk (PTA)

CyberArk Privileged Threat Analytics
PTA stands for Privileged Threat Analytics
And true to its name, CyberArk’s PTA is a modern system designed for privileged account security intelligence that provides detailed, immediate actionable threats analytics by pinpointing previously hidden malicious privileged user activity.

CyberArk PTA can boasts of being the only targeted privilege that analytics software in the industry, using copyrighted algorithms to identify dangerous threats aimed at privileged accounts. Proprietary algorithms identify imminent threats and alert the appropriate entities.
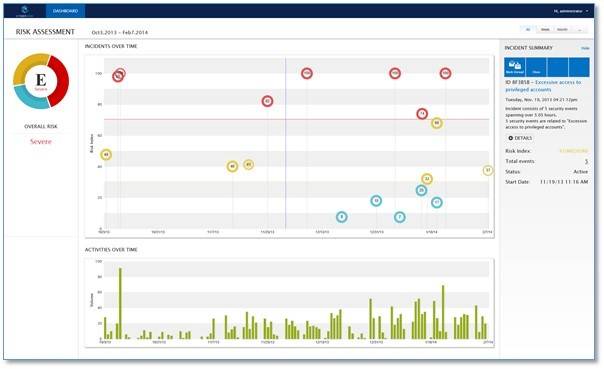
This patented analytic technology is applied to a unique set of privileged account behavioral data, and CyberArk PTA produces streamline and highly actionable intelligence that alerts the incident response teams to the point of attack. The data is also sent to existing SIEM solutions to upgrade the effectiveness of response and quality of alerts.
Why Choose CyberArk PTA
CyberArk has the honor of being the only company that can provide total protection against insider and advanced threats to eliminate risks and fulfill high-end compliance requirements. The product can boast of more deployments in large scale virtual and distributed environments, having solved many privileged account security issues than any other software solution.
We are here for you
Allow us to help you pick the best of breed solution for your IAM Issues
Data that Counts vs. All the Data
CyberArk’s PTA solution lays more emphasis on privileged account user data – data that counts. Usually, numerous security events take place in large enterprise IT organizations daily. Part of these events include many false positives that often leave the organization at a loss on how to choose the problems effectively: which threat is real and which risk should be overlooked?
CyberArk’s Privileged Threat Analytics software prioritizes the privileged accounts as they run the highest risk of damage.
Privileged Accounts vs. Privileged Users
In most cases, privileged accounts are shared accounts that can be accessed by multiple users. This hinders current event management software from attacking a specific activity to a particular user. CyberArk’s PTA assesses account behavior at the baseline level and delivers targeted context-aware, and actionable alerts.
Forensic Analysis vs. Real-time Updates
Standard forensic analysis on large amounts of underlying data produces relevant information on sensitive aspects of an organization’s operation but cannot provide real-time alerts on current threats. However, CyberArk’s PTA provides real-time updates that allow the incident response teams to take immediate action.
Patented Analytic Algorithms
Using proprietary algorithms that study the usual behavior of the privileged user, PTA compared old behavior to real-time privileged account activity to detect security anomalies as they happen. These unusual patterns are then cross-checked to determine if they possess malicious intent.
Integration with SIEM solutions
Apart from the proprietary dashboard preinstalled in the system, adapters and data from CyberArk’s PTA can be introduced into a company’s current SIEM system. The analytics on privileged user behavior promotes the efficiency of the SIEM system by activating targeted alerts on privileged account risks.
Detect, Alert and Eliminate Real-time Attacks
CyberArk Privileged Threat Analytics software solution utilizes user data to create a behavioral pattern for every user in the database and continually assesses their behavior over time to detect unusual changes in behavior. Once a baseline has been set, the CyberArk PTA software will search for any deviations from the usual behavioral patterns to identify abnormalities in privileged user behavior.
The software automatically identifies and rates each user’s anomaly, after which proprietary algorithms determine the credibility of each threat based on their relation to a potential cyber attack. Alerts can be sent through email detailing the incident type and will include a link to the PTA system where the appropriate team can review the report.
CyberArk Privileged Threat Analytics is continually learning about the environment it operates in to improve the efficiency and speed of its alerts. This ongoing adaptation provides clients with the most potent threat alerting system in the IT industry.
Benefits of CyberArk Privileged Threat Analytics
- Identify and cancel attacks with knowledge based on the history of user behavior, eliminating the reliance on sandboxing or history of attack signatures
- Drastically reduce the window of opportunity and damage that can be caused by an attacker with real-time alerts of current threats
- Promote the essence of current SIEM solutions with unconventional integrations
- Rerduce the number of false positives by prioritizing privileged users instead of shared accounts
- FastTrack remediation with instant access to comprehensive information about the attack
- Align threat detection to an evolving environment with artificially intelligent algorithms that continuously adjust the behavioral pattern as the environment changes
- Improved auditing process with comprehensive and detailed data
Pros
- The software interface is user-friendly
- The local workstation account management can delete local admin accounts and retain admin privileges
- Blocks unauthorized access, fulfills security requirements, and allows for detailed audit logs and reports
“To be honest, I can’t find a service that I dislike from GCA.”
– Sr. Director Of Infrastructure, Education on Gartner Peer Insights
![]()
Start Planning For the Future Today
Book a 15-minute call with a GCA representative today to find out how an assessment can help you combat the challenges your organization is facing. We’ll discuss the interview process and set expectations for stakeholders.
Book a 15-minute IAM expert to get started.
